Data Policy
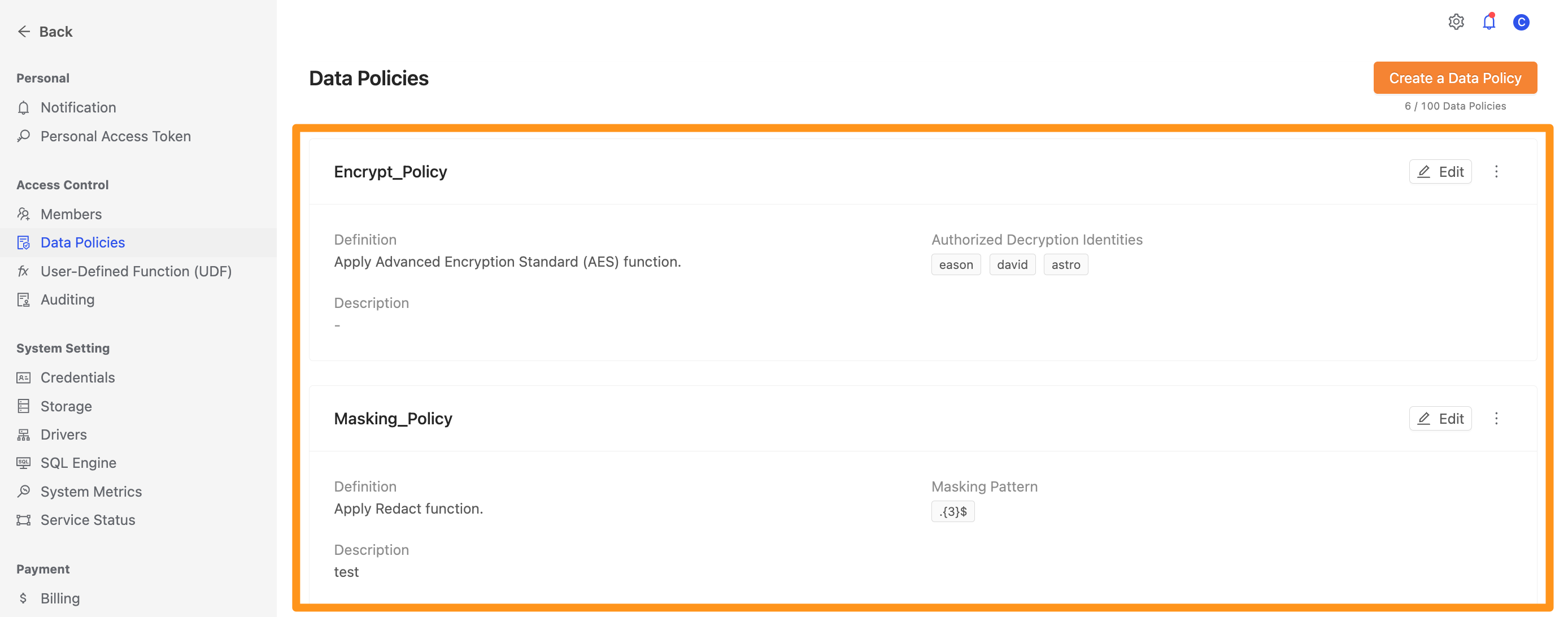
Data Policy helps enterprises define unified data privacy and data access control policies on the platform.
Setting Data Policy
You can configure Data Policy on the Data Policies page. Data Policies can be applied to data sources or tables in the workspace.
Data Policy only supports a maximum of 100 rules
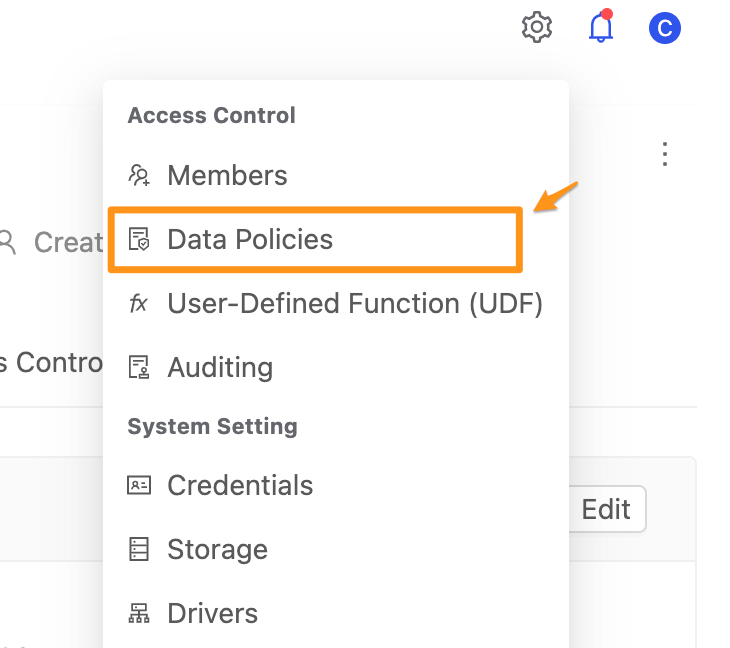
Step 1: Enter Data Policies page
Click the settings icon in the upper right corner and select Data Policies.
Only admin users have the permission to create Data Policy.
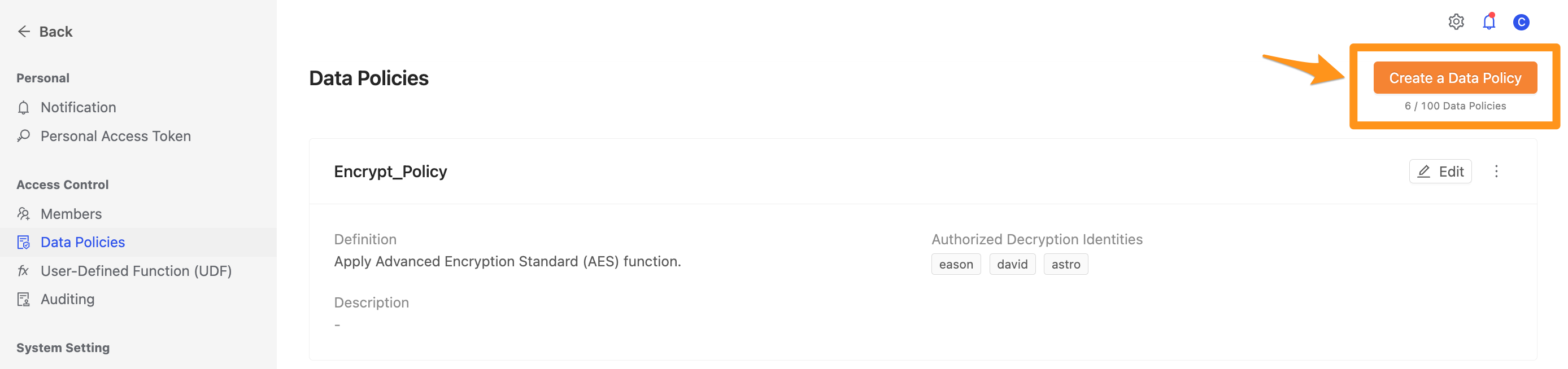
Step 2: Create a Data Policy
After entering the Data Policies page, click the Create a Data Policy button.
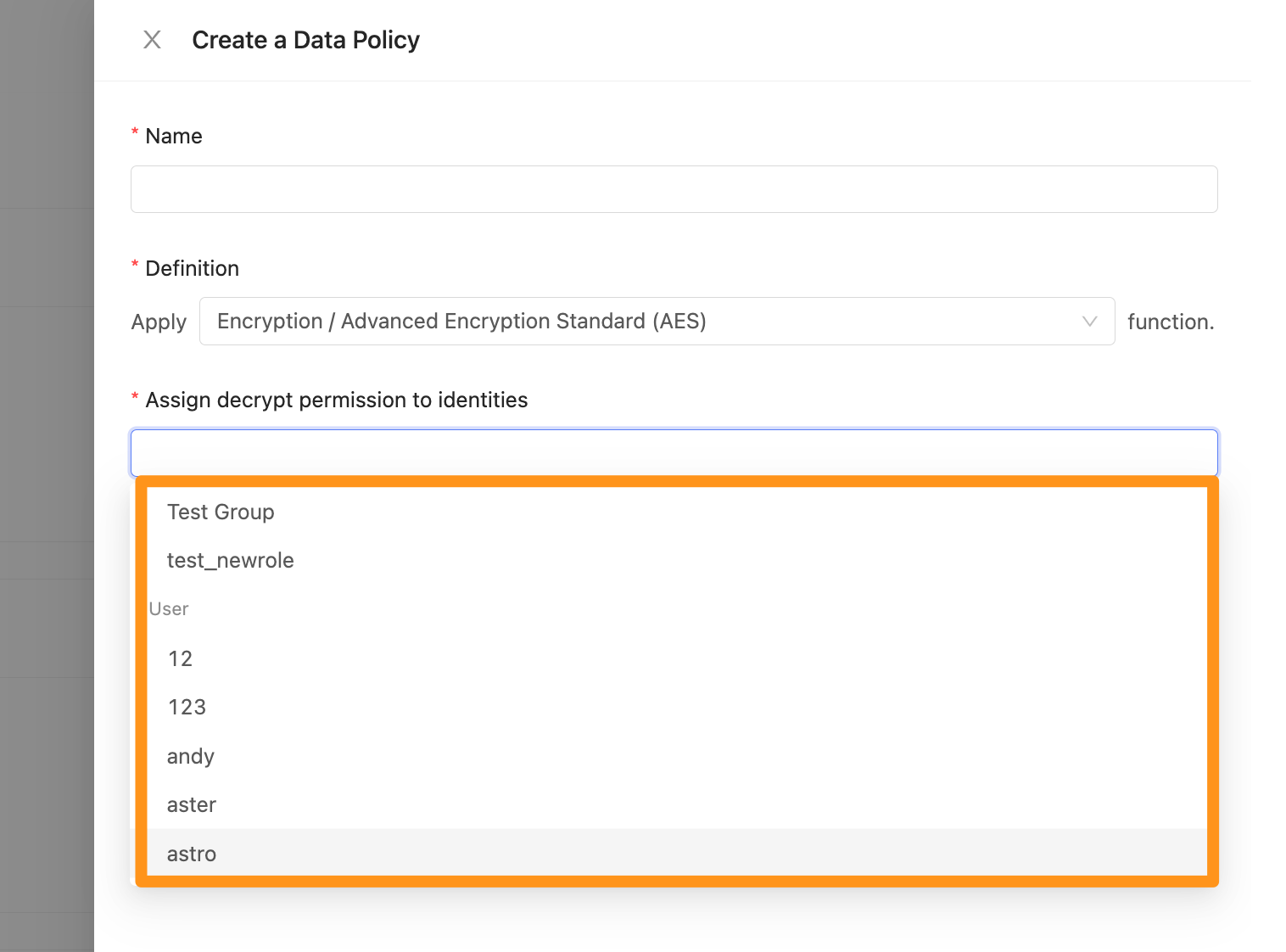
By filling up the form below to create a new policy.
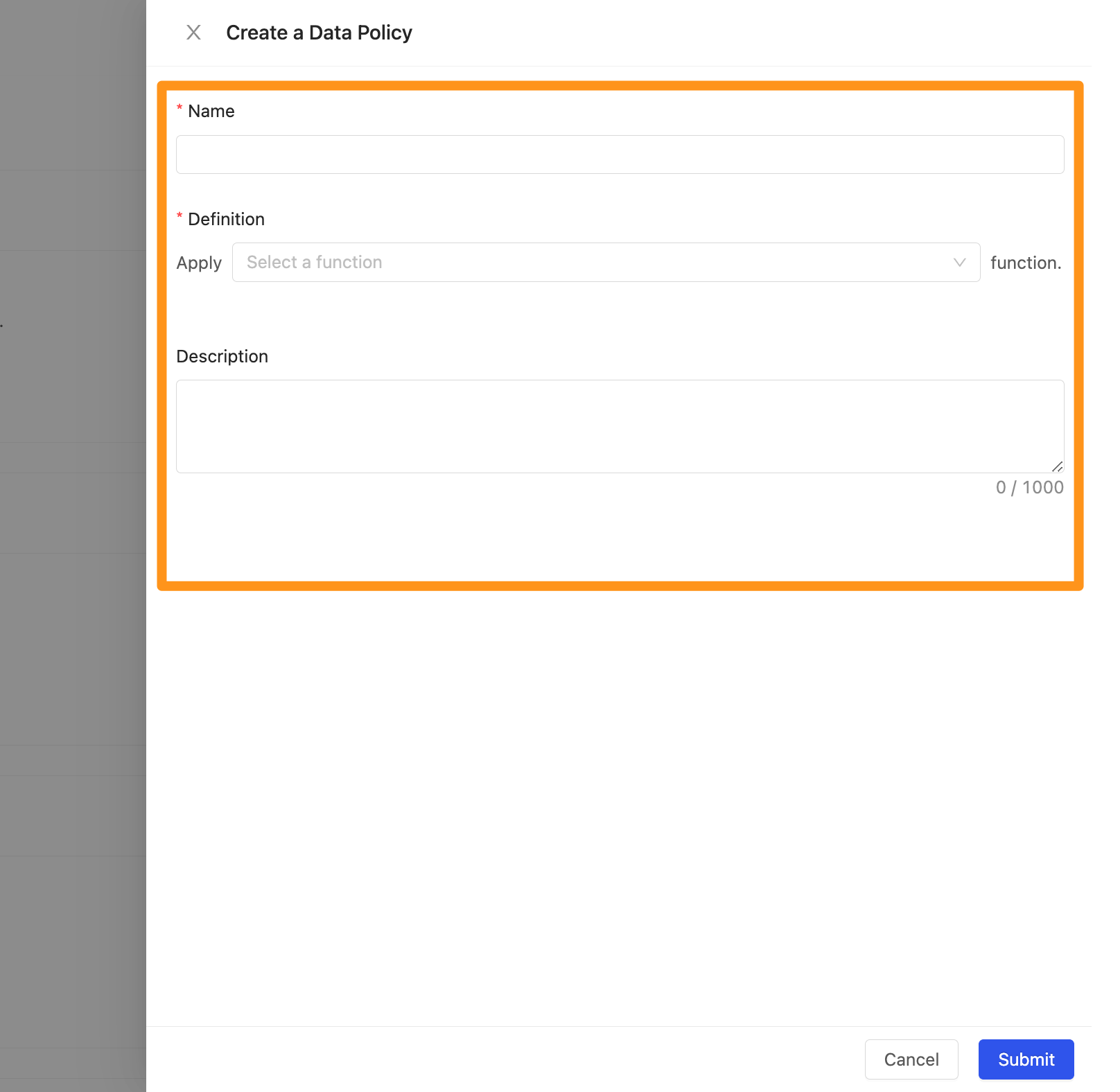
- Name: Display name of the Policy, it can be changed afterwards.
- Definition: The data encryption method used by Policy
- Contains Masking, Hashing, Encryption
- Description: You can add a description of this data policy.
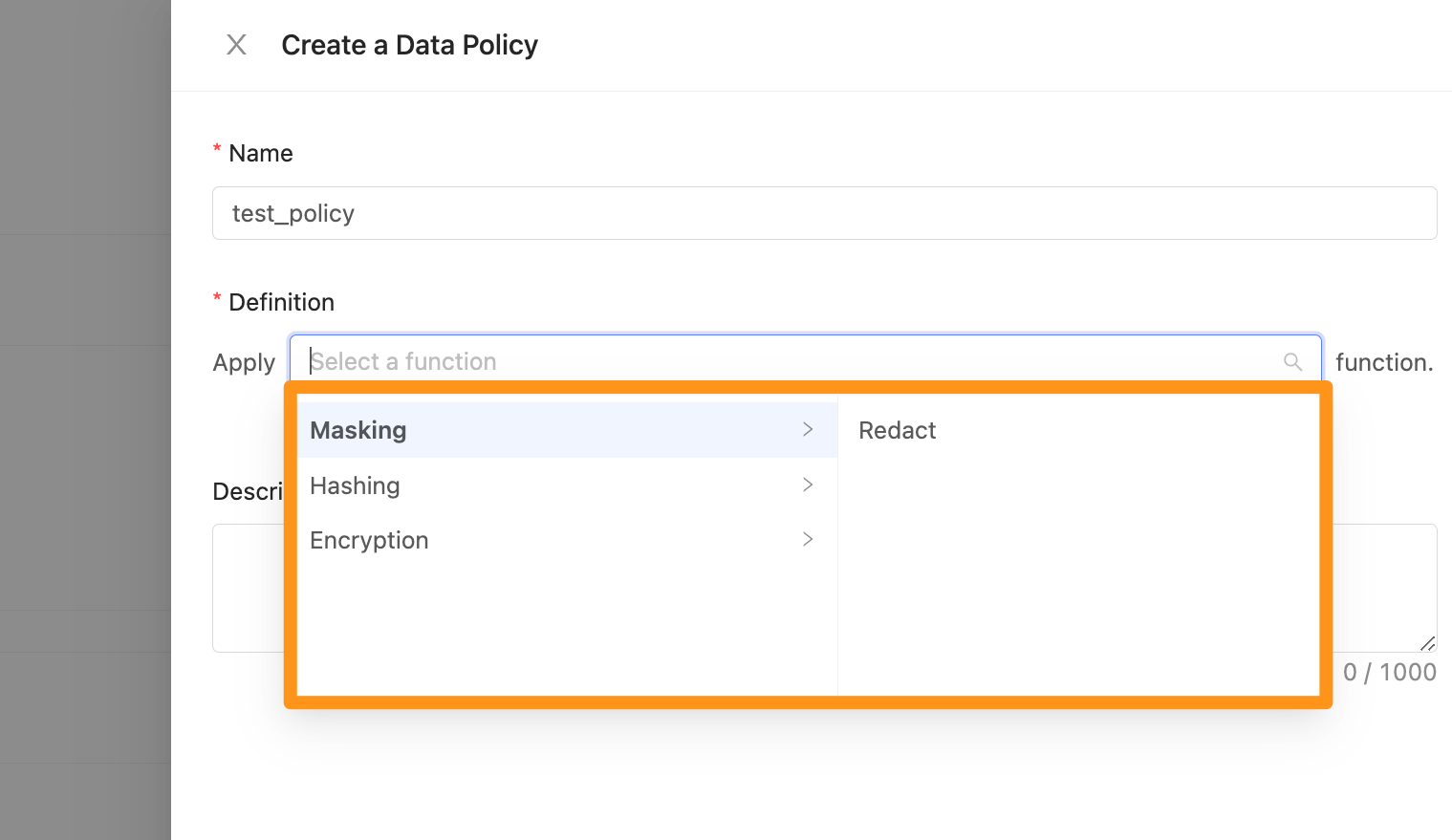
Select Masking data encryption method
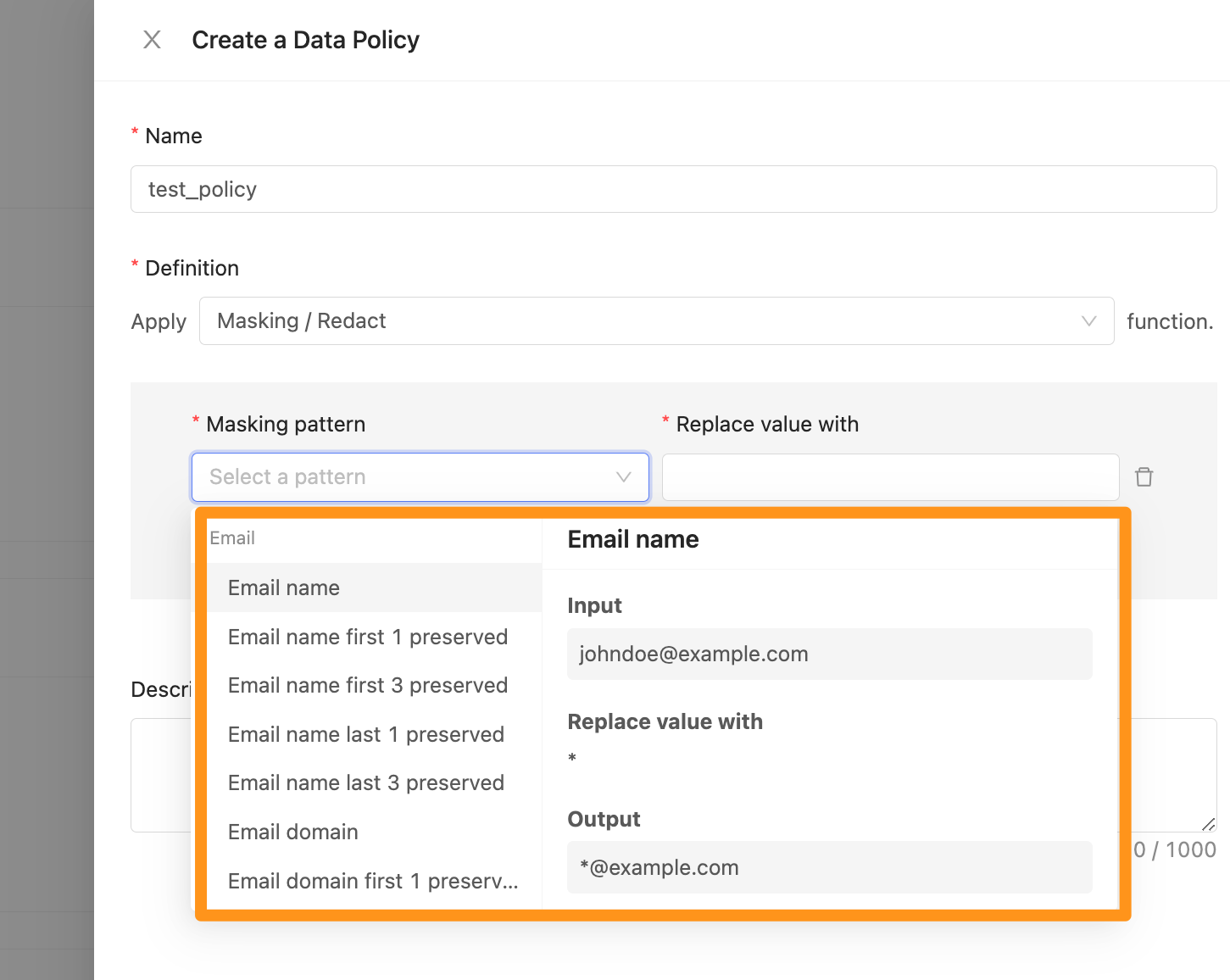
Masking pattern: The system provides built-in masking patterns, including six different data types such as Email, Identification Number, Data of birth, Name, Phone Number, etc., and you can apply up to 2 patterns. It should be noted that the attached patterns are executed sequentially.
Replace value with: The value to be replaced
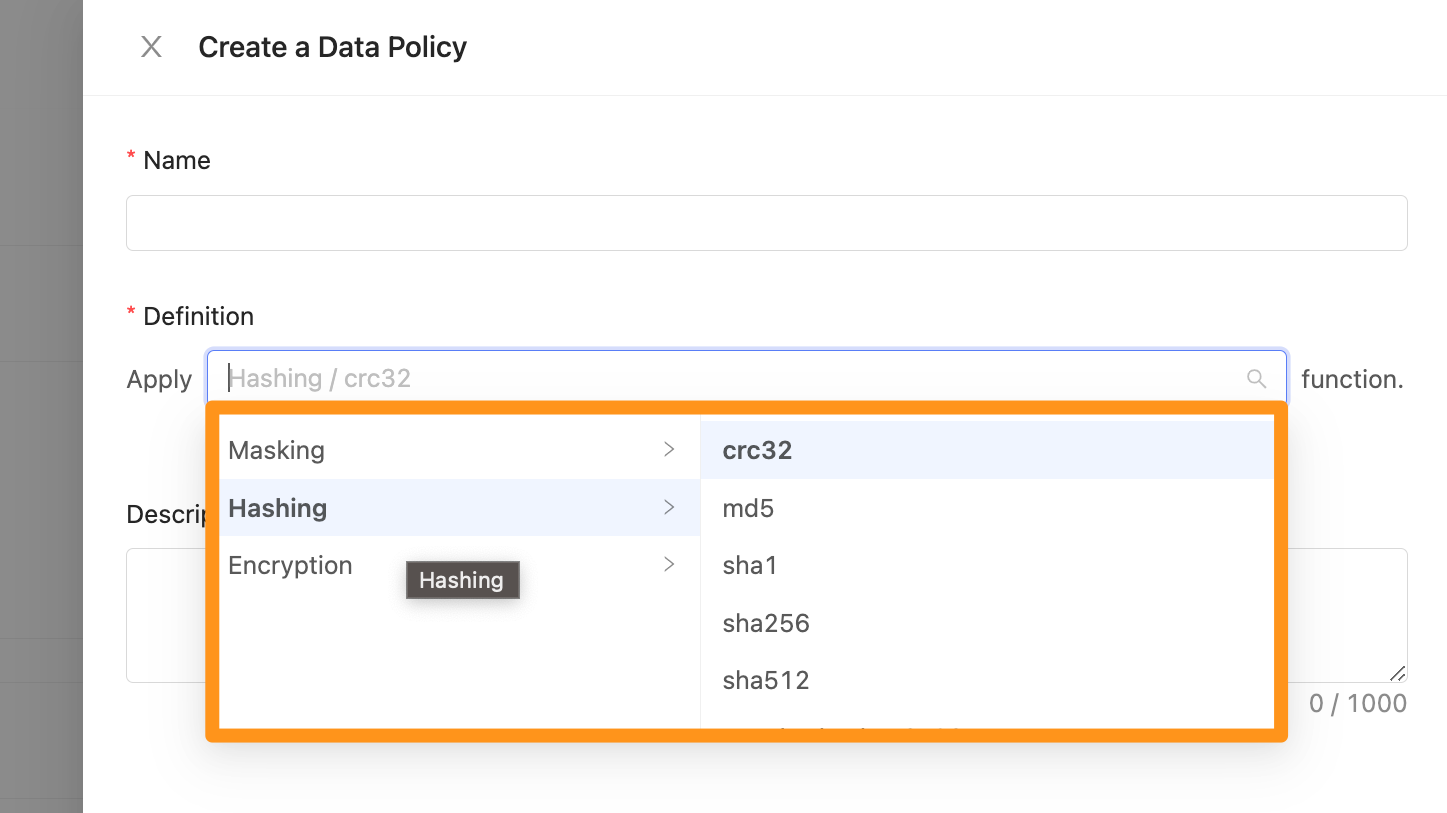
Select Hashing data encryption method
Select Encryption data encryption method
Provides
AES,PBE,RSAencryption methodsPrecautions for using RSAPay special attention to the fact that when using the
RSAencryption method, the number of fields must be controlled within 200 bytes. Exceeding the limit will cause encryption to fail. In addition,RSAis a high-strength encryption method, so it requires a long execution time when encrypting or decrypting. The time required depends on the length of the data.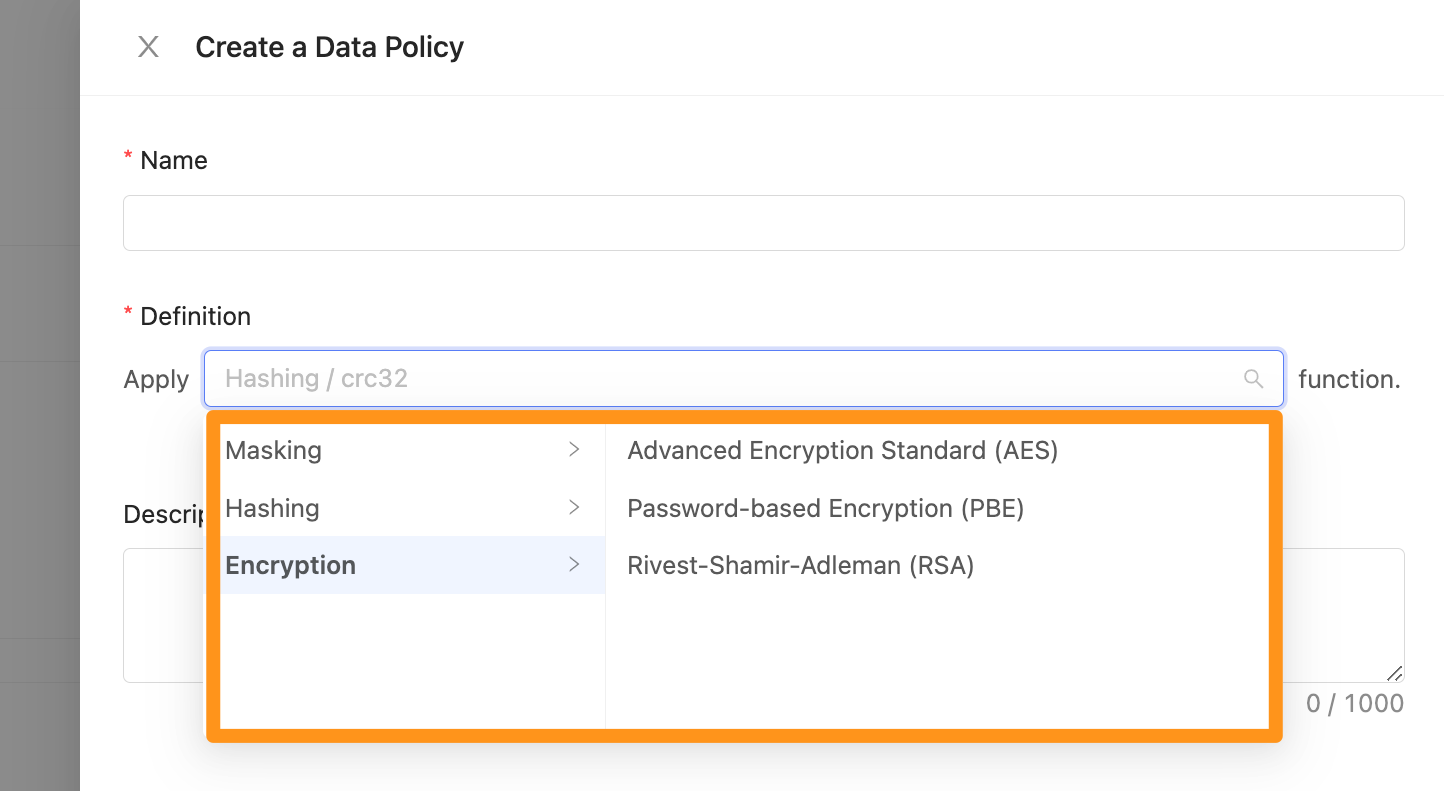
- Assign decrypt permission to identities: Authorize Group and User with decrypt permission. Be noted that the person who sets the Data Policy does not have decryption permissions and needs to be authorized to decrypt the data.
Step 3: Complete the creation of Data Policy
After clicking Submit, you can see all currently created Data Policies on the screen.