LDAP
You can seamlessly integrate Canner Enterprise with LDAP, such as Microsoft Active Directory, OpenLDAP, etc.
In below example, we use JumpCloud as an example in this case.
1. Obtain Necessary Information
In this section, we will use the JumpCloud platform to obtain the required information. Please ensure that you have registered and logged into JumpCloud and have created an organization.
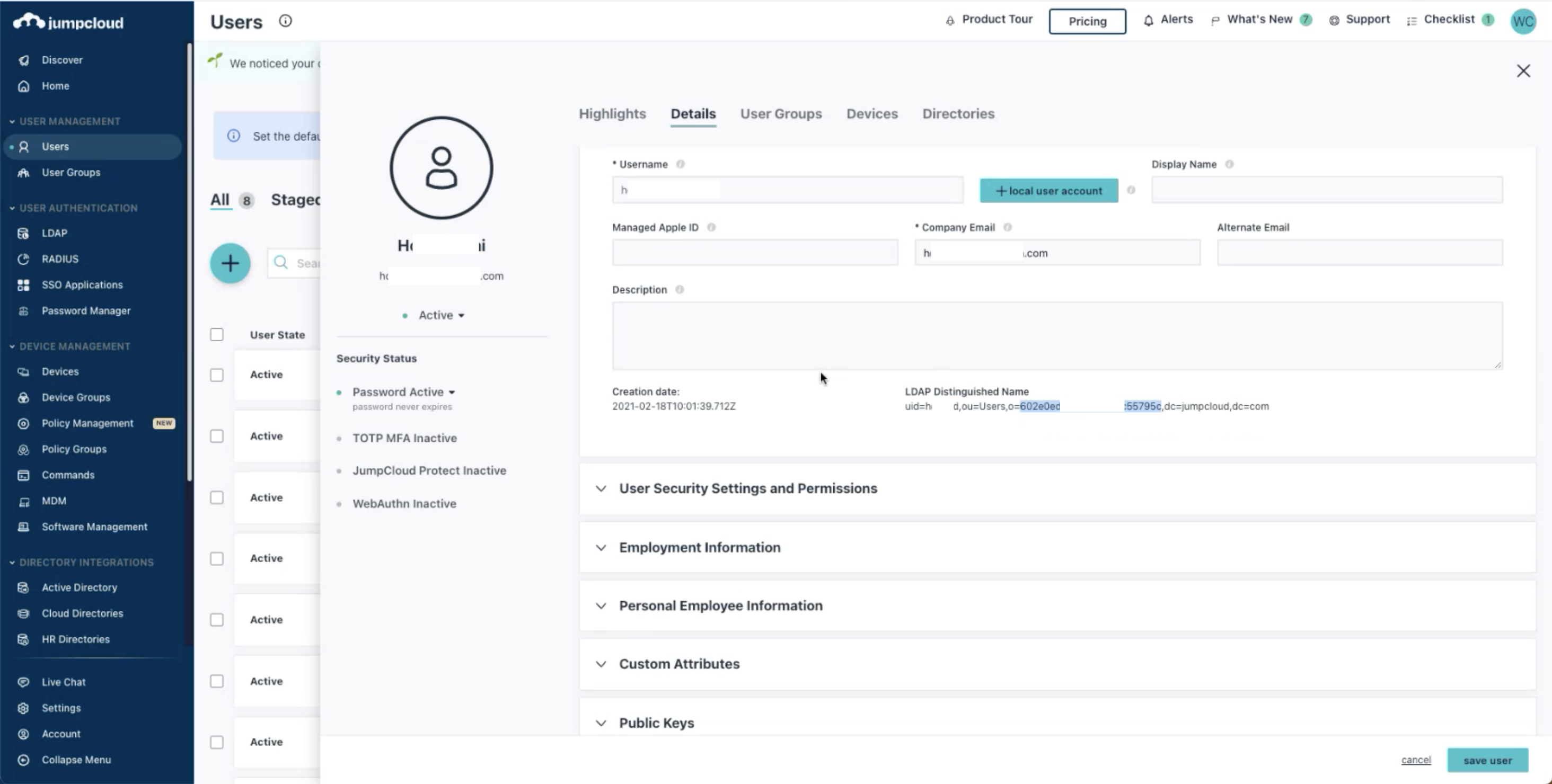
To synchronize information with Kyycloak, we need to obtain theUsers DNandBind DN.
The Users DN is usually ou=Users,o={organizationId},dc=jumpcloud,dc=com and can typically be found on JumpCloud's LDAP settings page.
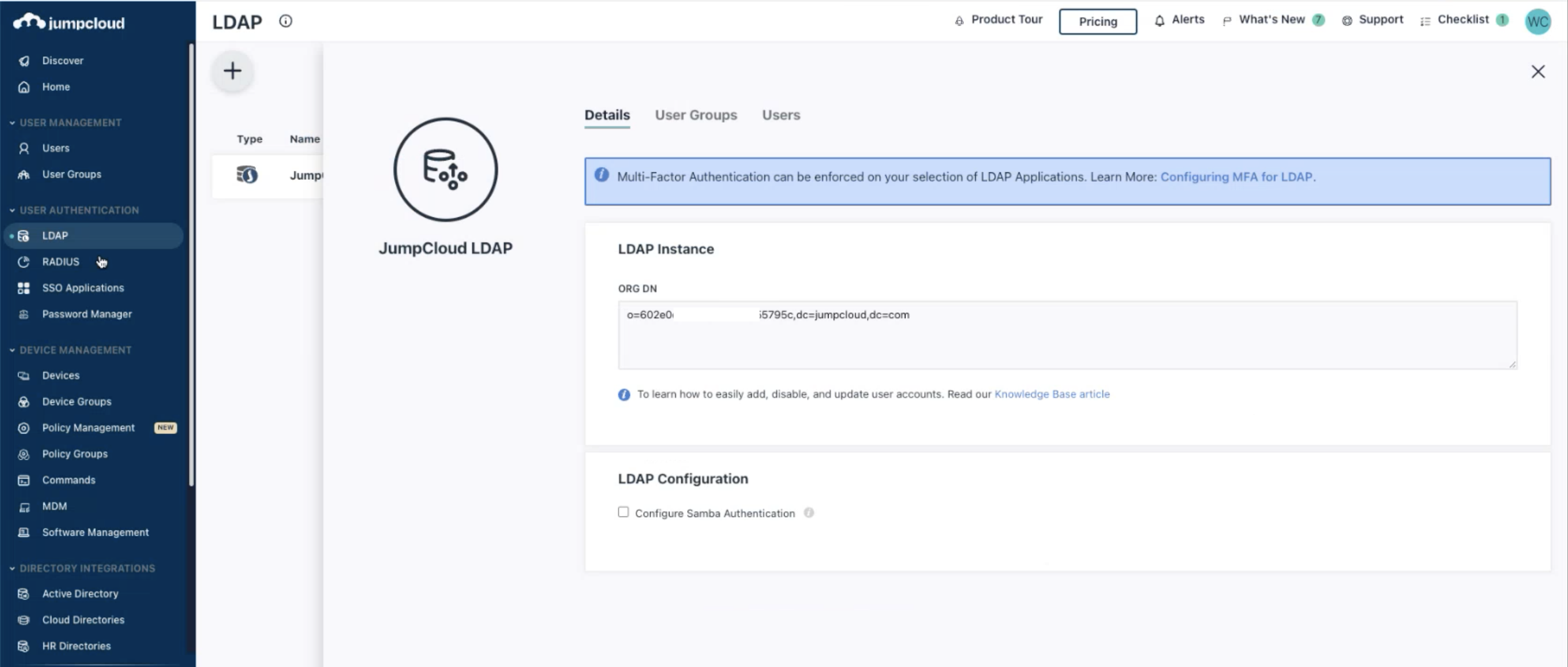
The Bind DN is usually uid={username}.ou=Users,o={organizationId},dc=jumpcloud,dc=com and can be found in the User Detail section on JumpCloud's User page.
2. Connection Configuration
Before logging into Keycloak, obtain Keycloak login credentials from the system administrator of Canner Enterprise.
In a Standalone environment, the Keycloak login path ishttp(s)://{host}/sso/auth.
Basic Configuration
Log in to the Keycloak Administration Console and ensure that the Realm settings are correct.
In the left menu, select Configure > User Federation. On the User Federation page, choose Add provider and select LDAP.
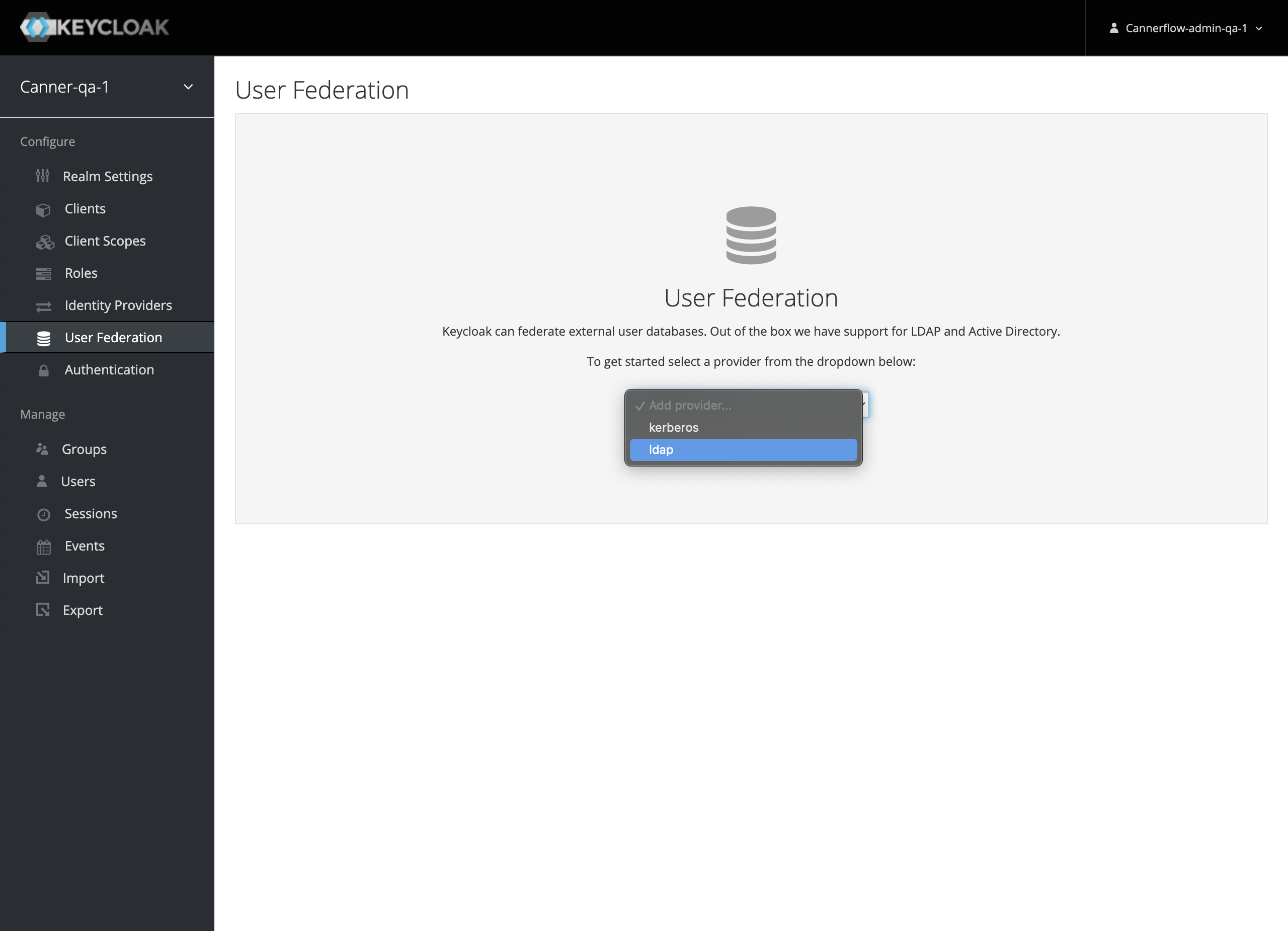
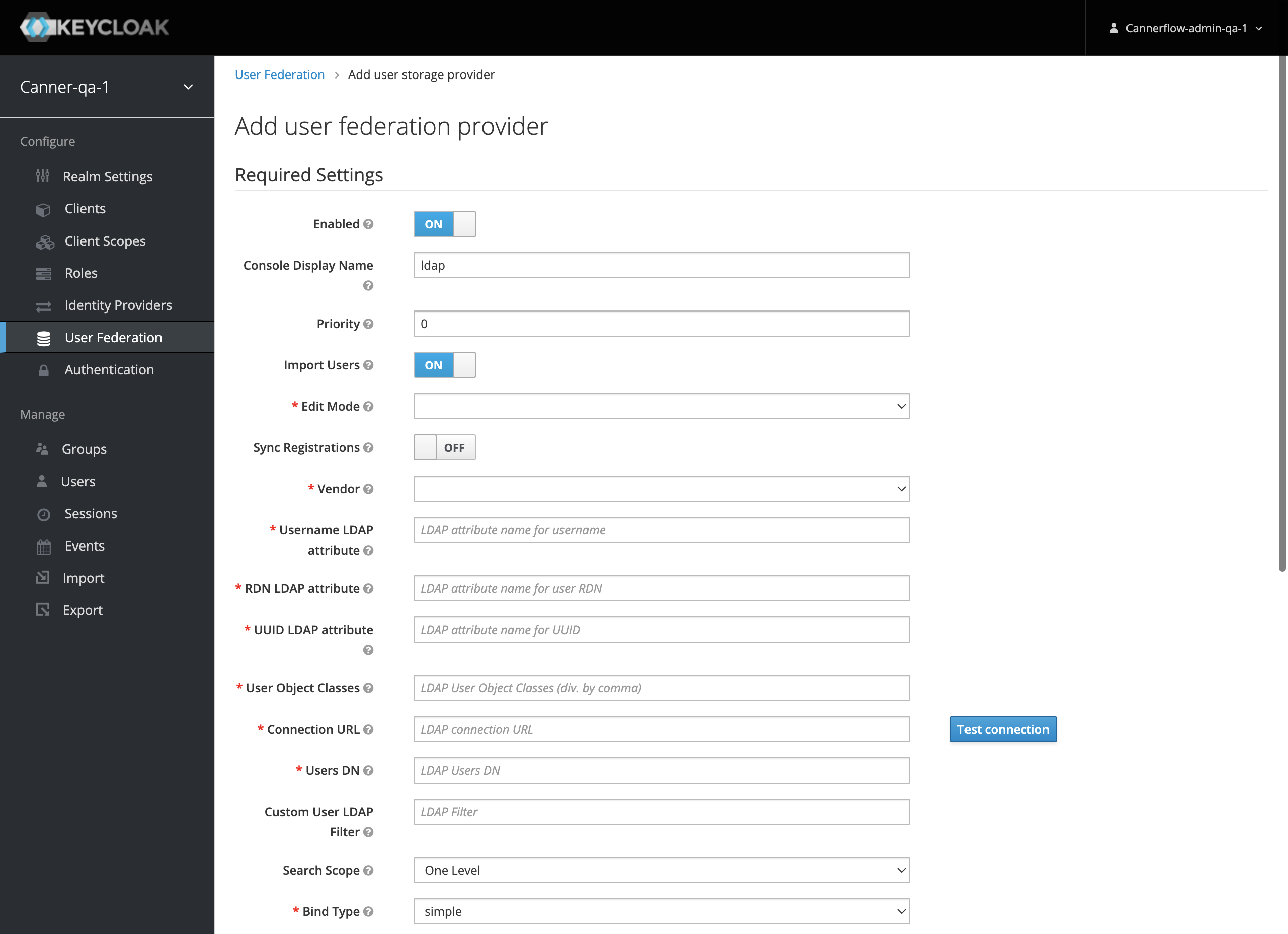
LDAP Field Descriptions
| # | Field Name | Description | Example Input |
|---|---|---|---|
| 1 | Console Display Name | Display Name | ldap |
| 2 | Priority | When there are multiple providers in the same Realm, the provider with a smaller number takes precedence. | 0 (default) |
| 3 | Import Users | If set to "On," users from Windows AD will be synchronized to Keycloak's database. | On (default) |
| 4 | Edit Mode | – READ_ONLY: Sync from LDAP to Keycloak, data cannot be updated in Keycloak – WRITABLE: Bidirectional sync between Keycloak and LDAP – UNSYNCED: Sync from LDAP to Keycloak, data can be updated in Keycloak | UNSYNCED |
| 5 | Sync Registrations | If set to "On," newly added LDAP users will be immediately synchronized to Keycloak. | OFF (default) |
| 6 | Vendor | Provider of directory or authentication. | Other |
| 7 | Username LDAP attribute | LDAP attribute for the logged-in account, usually cn or uid. | cn (default) |
| 8 | RDN LDAP attribute | Corresponds to the LDAP RDN attribute, usually cn. | cn (default) |
| 9 | UUID LDAP attribute | Corresponds to the LDAP UUID attribute used to map a single account, usually objectGUID. | objectGUID (default) |
| 10 | User Object Classes | Specifies the attributes of the User, usually person, organizationalPerson, user. | person, organizationalPerson, user (default) |
| 11 | Connection URL | Network location of Windows AD (or LDAP), usually starts with ldap://. | ldap://{IP or hostname} |
| 12 | Users DN | Specifies all objects under a certain node, usually specifies an OU. | ou=Users,o=602e0xxxxxxxxxxxxc55x9bc,dc=jumpcloud,dc=com |
| 13 | Custom User LDAP Filter | If filtering specific attributes, specify in this field. | Refer to LDAP Query Syntax |
| 14 | Search Scope | – One Level: Reads only Users DN at the same level – Subtree: Reads all levels below Users DN | Subtree |
| 15 | Bind Type | Specifies the authentication method for Windows AD (or LDAP), simple indicates the use of username/password. | simple |
| 16 | Bind DN | Specifies the authentication account for Windows AD (or LDAP). | uid=canner-qa.ou=Users,o=602e0xxxxxxxxxxxxc55x9bc,dc=jumpcloud,dc=com |
| 17 | Bind Credential | Password for the authentication account of Windows AD (or LDAP). | ******** |
Test Connection and Authentication
- On the right side of the screen, there are "Test connection" and "Test authentication" buttons. These buttons provide connection and authentication tests. Once both tests pass, click "Save" at the bottom.
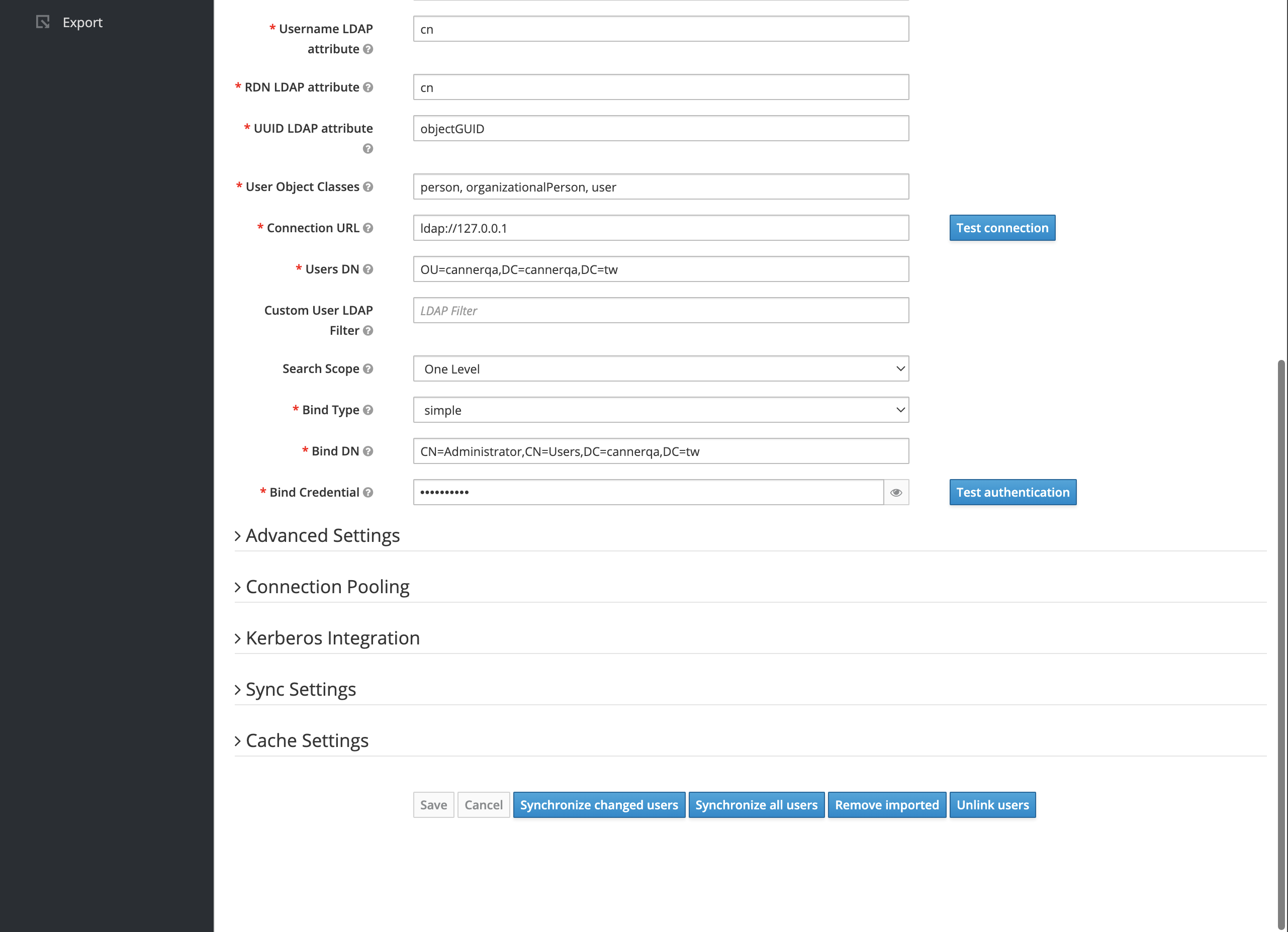
2. Grant Basic Permissions for LDAP User
Canner Enterprise has strict requirements for customer data security and permission control. Therefore, each user must have basic permissions to use Canner Enterprise services.
This step will establish basic permissions for LDAP users.
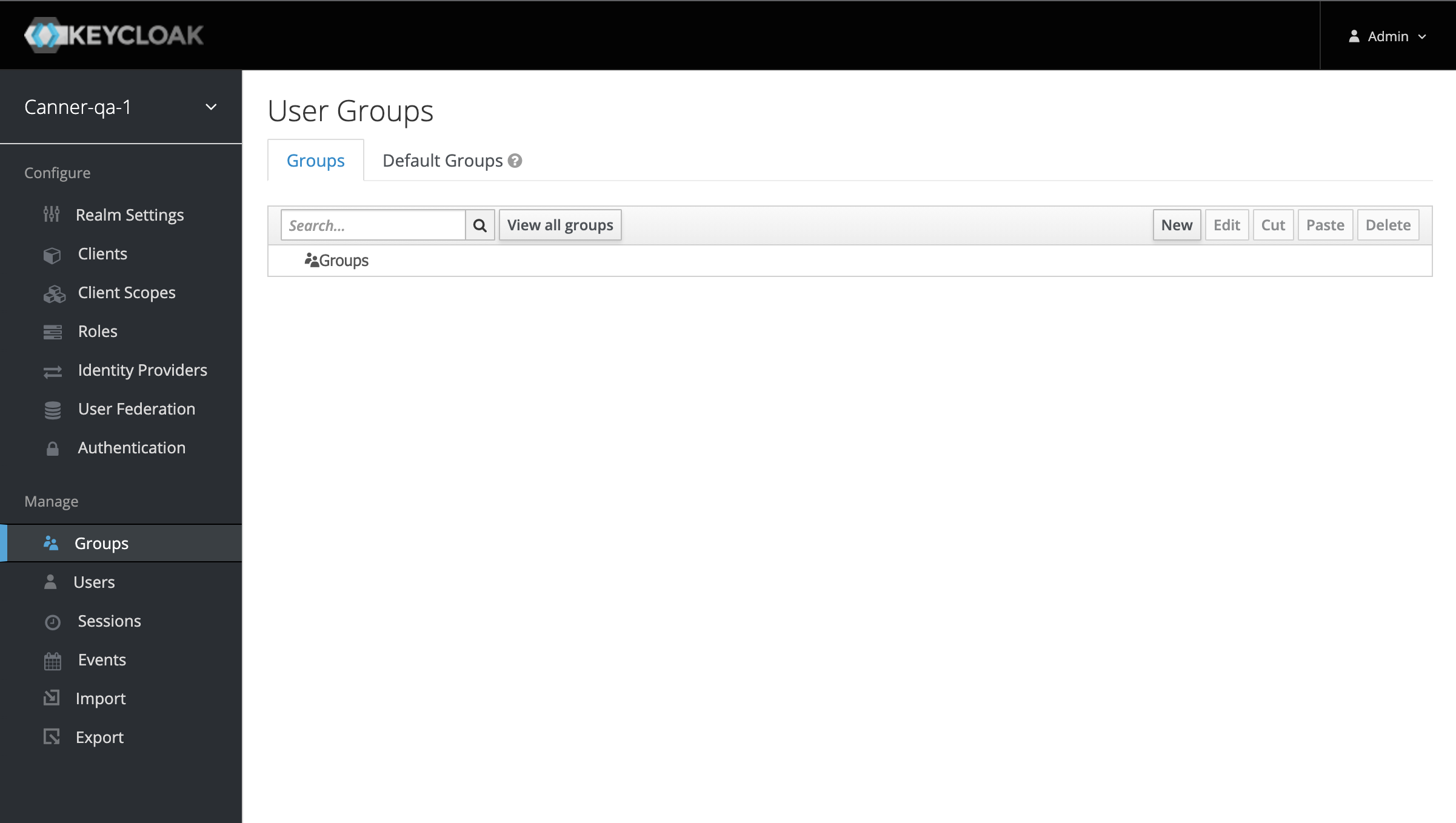
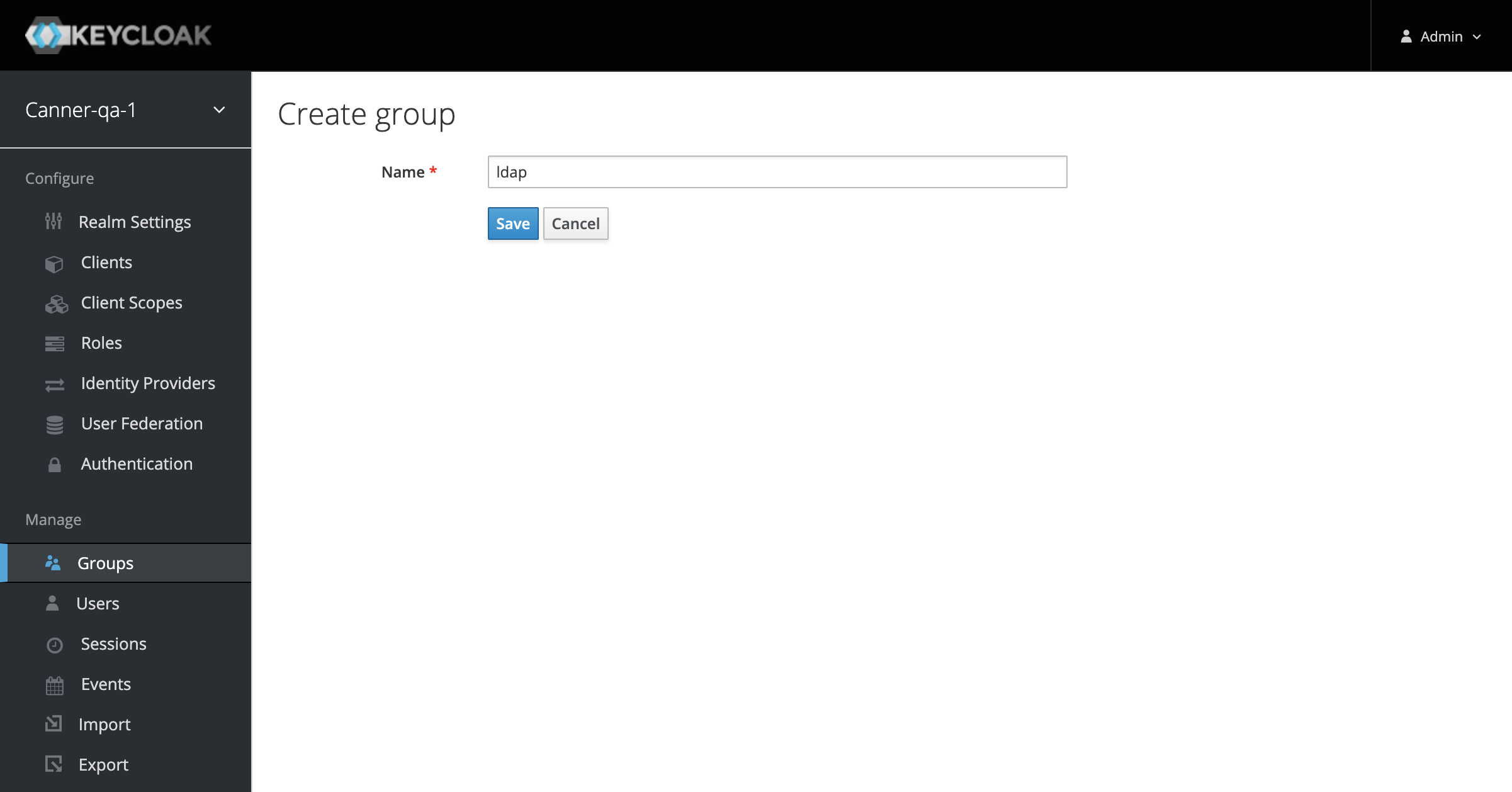
Create Group
- Before clicking "Synchronize all users" to sync users to Keycloak, go to the User Groups from the left-side Groups menu and click "New" to create a group in preparation for later user synchronization.
Establish Basic Permissions for the Group
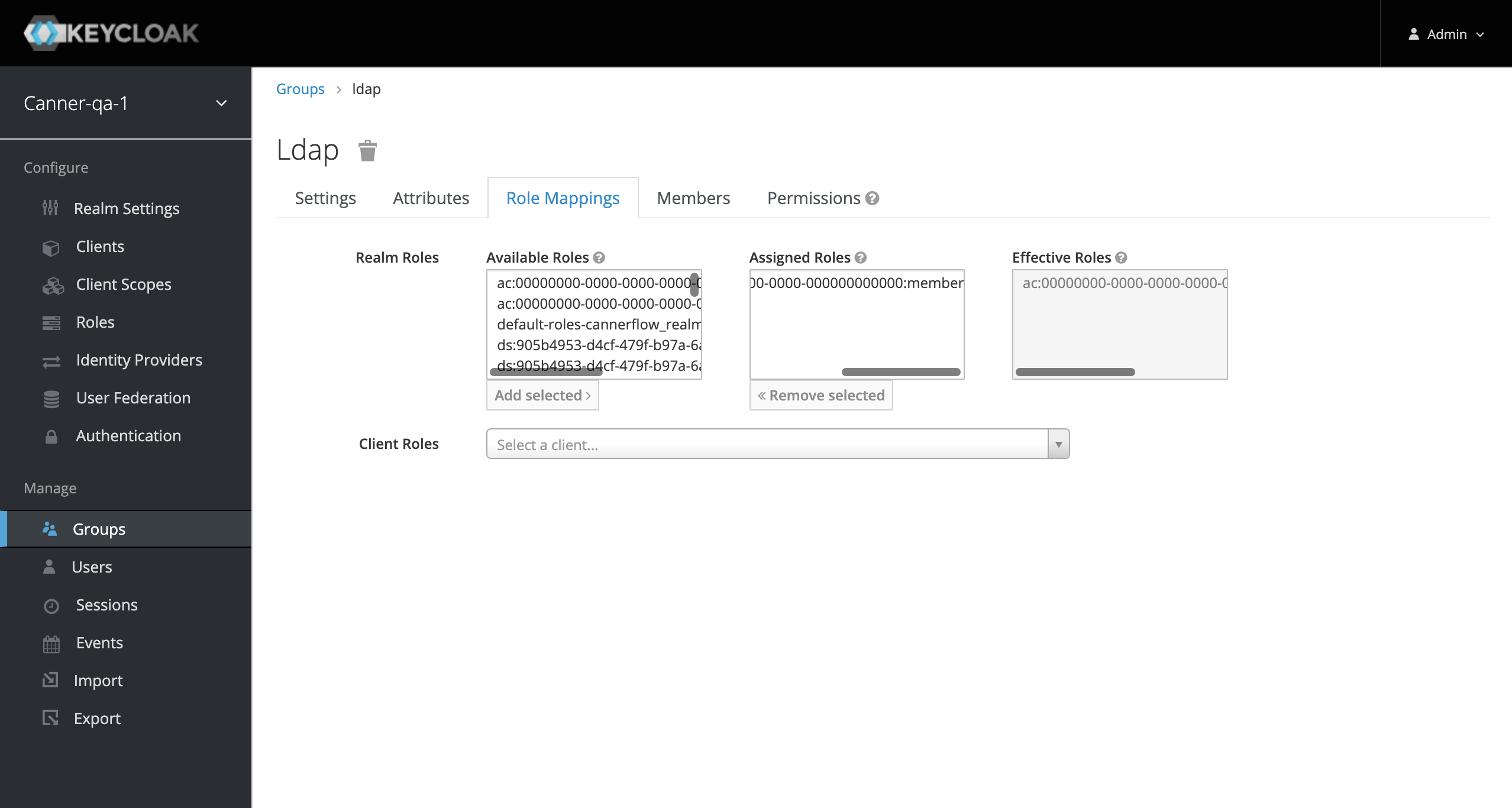
- After creating the group, click the Role Mappings tab and move
ac:{uuid}:memberfrom Available Roles to Assigned Role.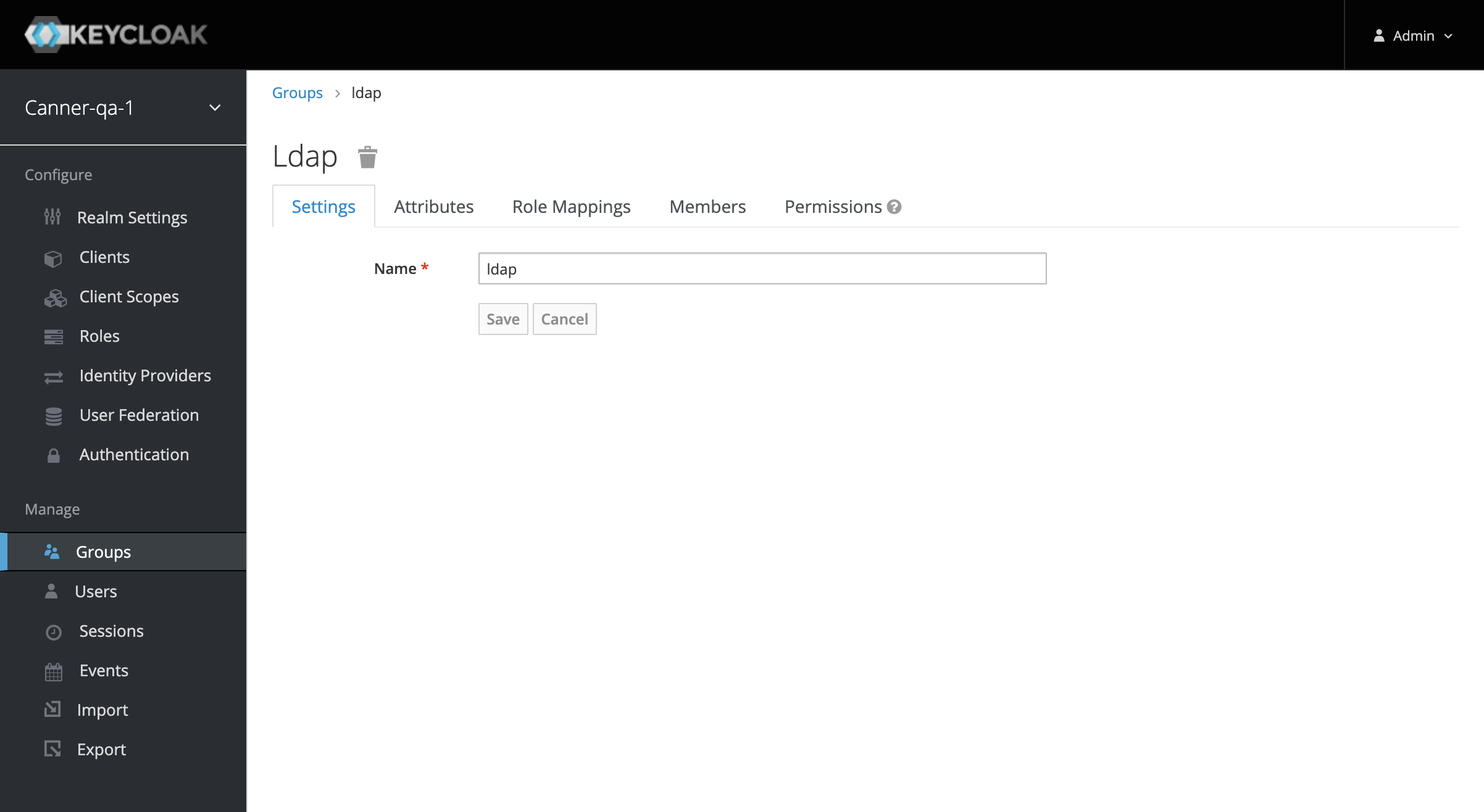
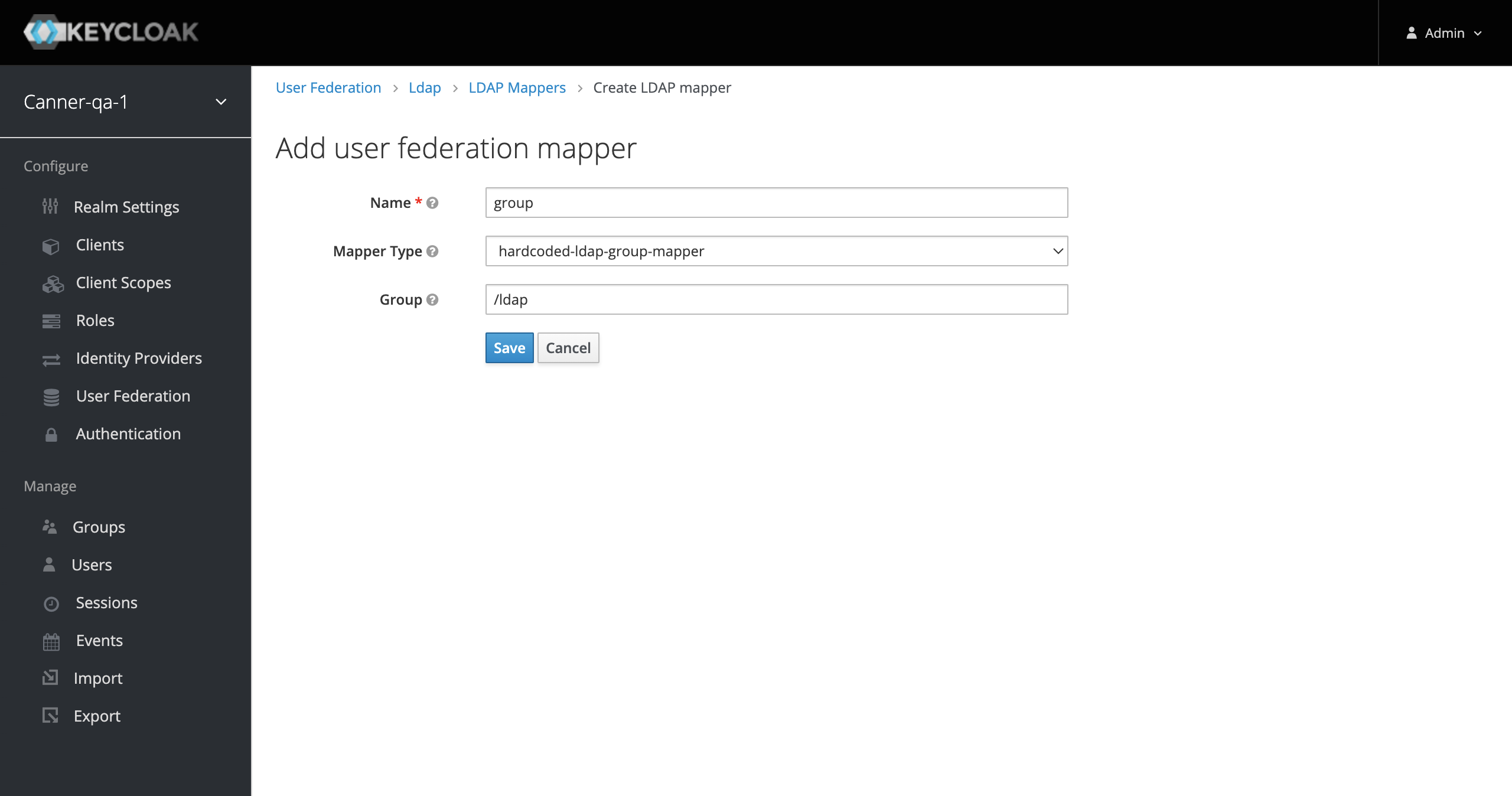
Create Mapper
Go back to User Federation > LDAP and click on the Mappers tab. Switch to the LDAP Mappers page and click the "Create" button.
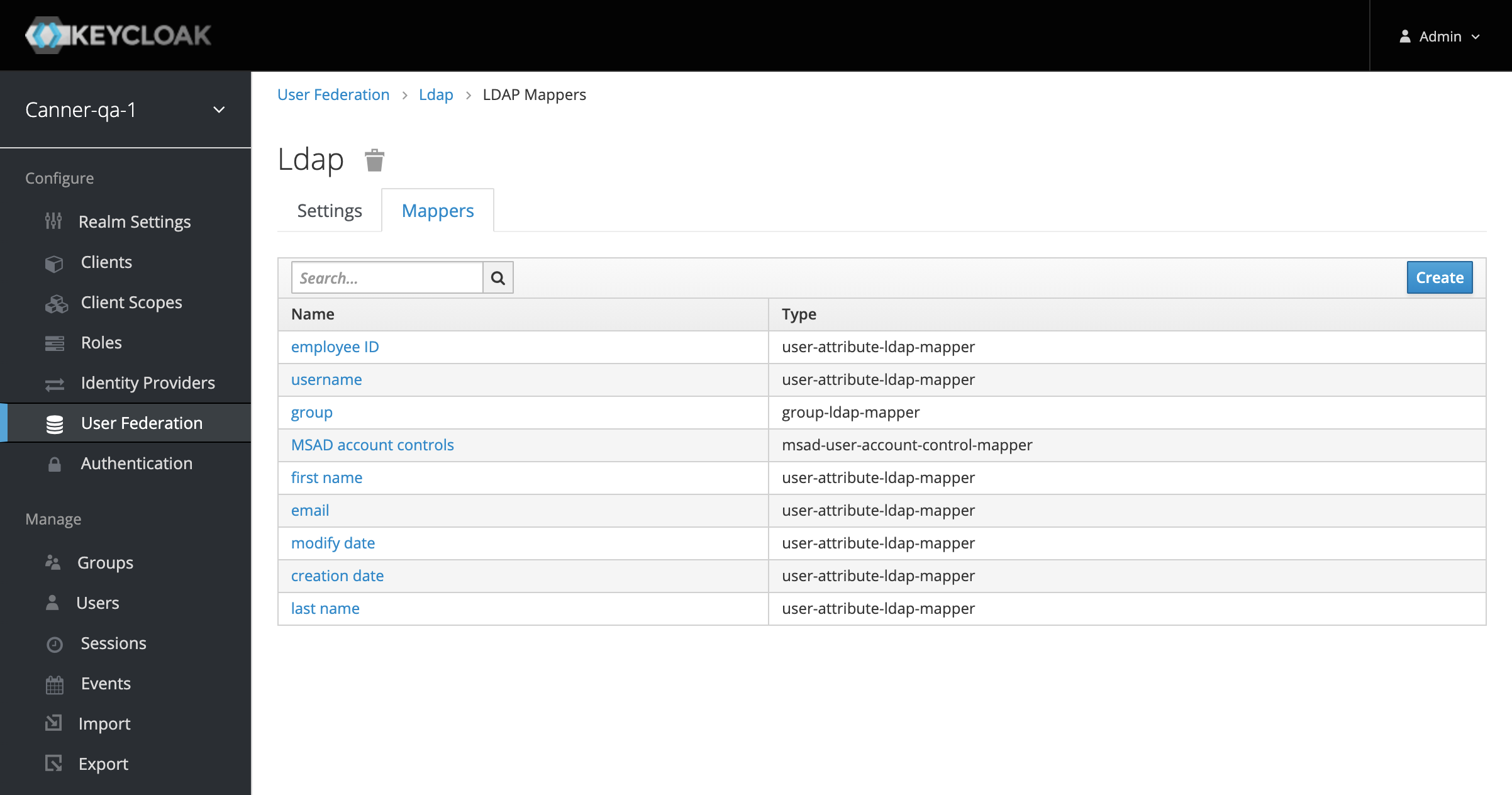
As shown in the image, select
msad-user-account-control-mapperforMapper Typeand enter the group name created earlier in theGroupfield. Click "Save" to store the configuration.
Synchronize Users
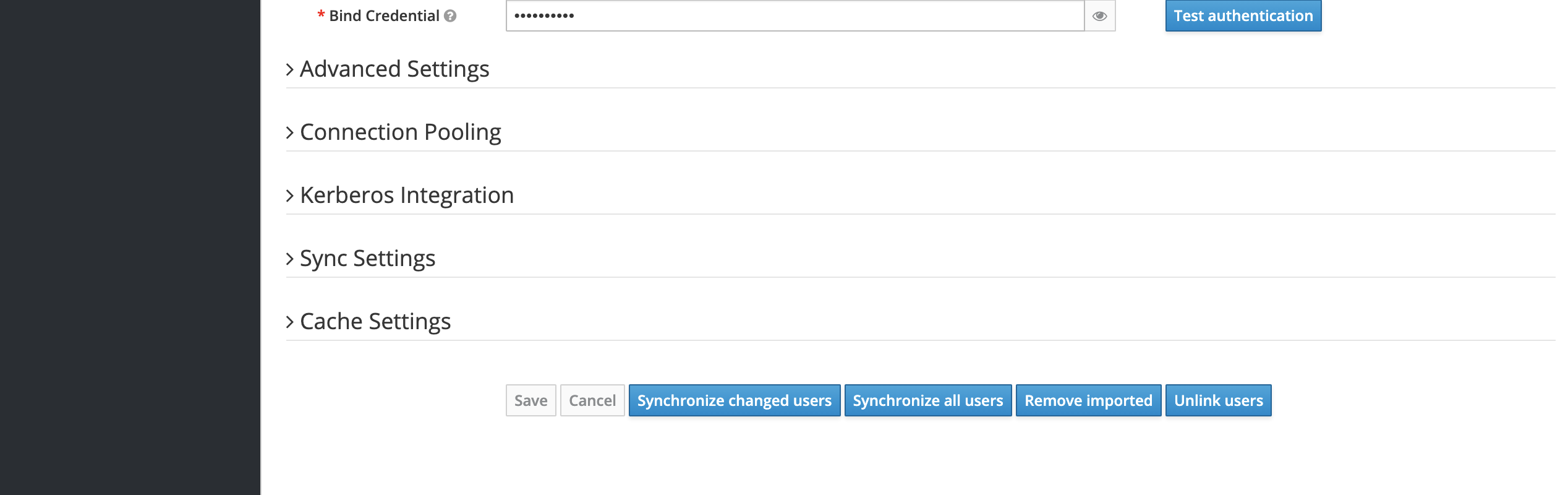
- Finally, return to User Federation > LDAP and click the "Synchronize all users" button at the bottom to sync all users to Canner Enterprise.
Test Login
After completing the above steps, you can log in to Canner Enterprise using the LDAP user's account credentials.
The Canner Enterprise login path is
http(s)://{host}/web.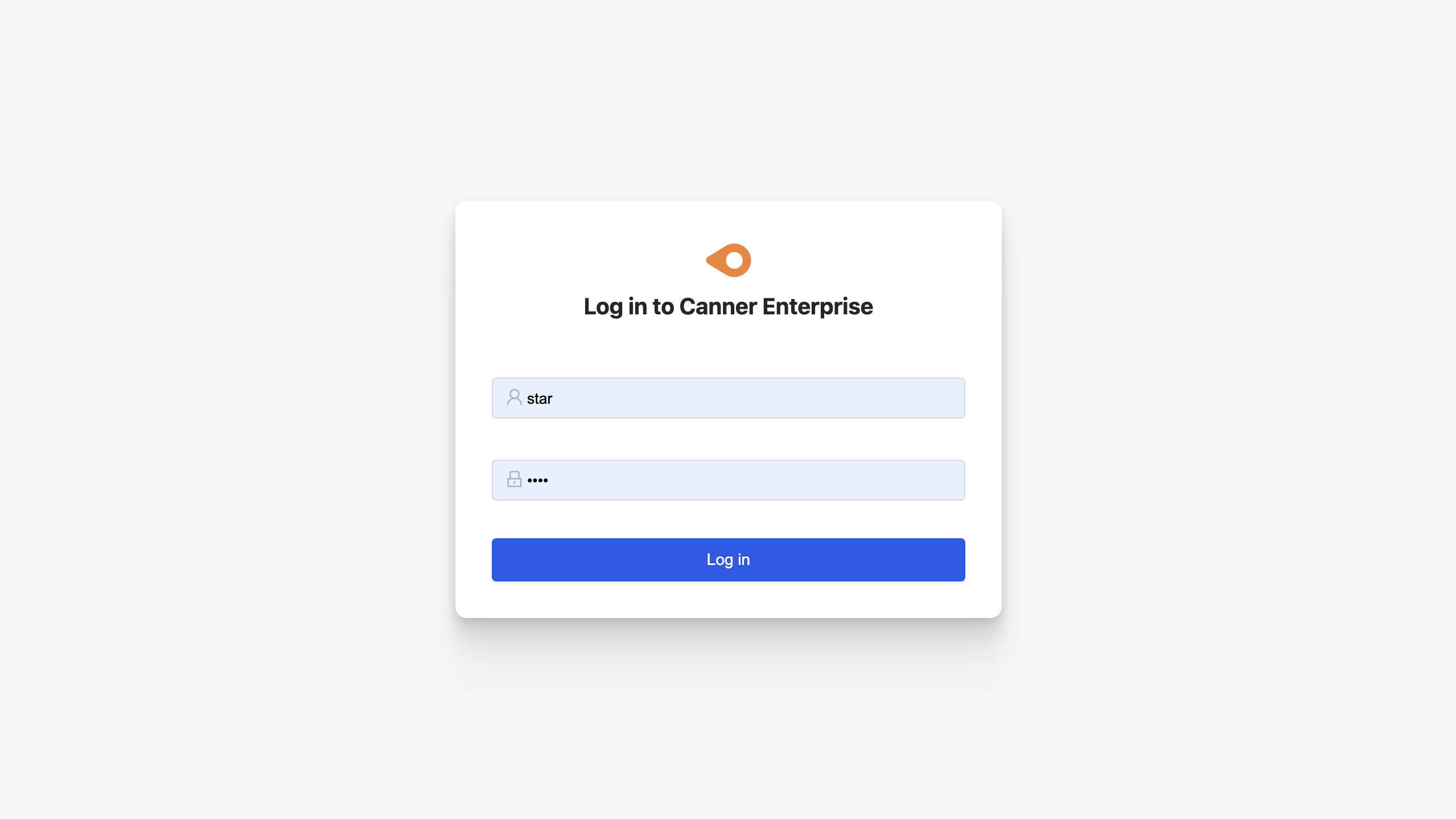
Upon successful login, you'll see the homepage of Canner Enterprise.